可私人定制的勒索病毒——BlackCat
2021-12-30
威胁等级:★★★★
近期瑞星安全研究院捕获到一个采用Rust语言编写的勒索病毒BlackCat,该勒索病毒曾在俄语黑客论坛进行过公开推广。该勒索软件通过命令行调用,可灵活配置绝大部分参数。勒索采用RSA+AES/ChaCha20的方式加密磁盘文件,在未获得密钥的情况下暂时无法解密。
概述
近期瑞星安全研究院捕获到一个采用Rust语言编写的勒索病毒BlackCat,该勒索病毒曾在俄语黑客论坛进行过公开推广。该勒索软件通过命令行调用,可灵活配置绝大部分参数。勒索采用RSA+AES/ChaCha20的方式加密磁盘文件,在未获得密钥的情况下暂时无法解密。
根据勒索团队的说法该勒索软件支持2种文件加密算法,4种加密模式。以下是勒索团队部分描述的机器翻译结果:
该软件是从头开始编写的,没有使用任何模板或之前泄露的其他勒索软件的源代码。提供选择:
4 种加密模式:
-Full - 全文加密。最安全,最慢。
-Fast - 加密前 N 兆字节。不推荐使用,这是最不安全的可能解决方案,但速度最快。
-DotPattern -
通过M步对N兆字节进行加密。如果配置不正确,Fast在速度和密码强度方面的工作可能更差。
-自动- 根据文件的类型和大小,locker(在windows和* nix / esxi上)会选择最优的(速度/安全方面)策略来处理文件。
-SmartPattern - N兆字节的百分比步骤加密。默认情况下,它从文件头开始,每10%加密10兆字节。速度/密码强度比的最优模式。
2种加密算法:
-ChaCha20
-AES
在自动模式下,软件检测是否存在AES硬件支持(存在于所有现代处理器中)并使用它。如果不支持AES,则对ChaCha20进行加密。
样本信息
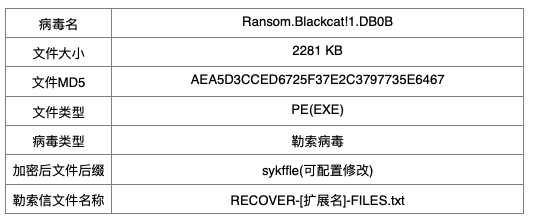
详细分析
样本文件提供命令行参数选项以实现个性化的勒索攻击
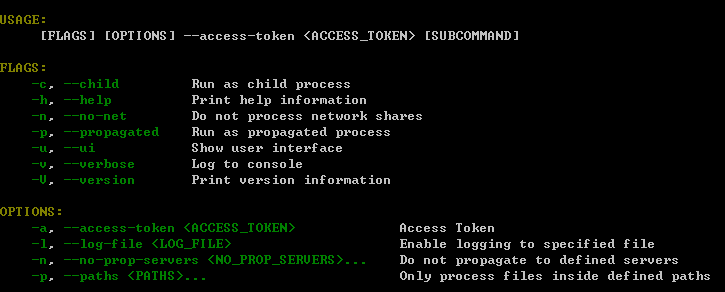
该勒索硬编码一个JSON格式的config作为勒索的初始默认配置文件,在未指定配置文件时将被读取并使用。以下是当前分析样本的配置文件:
{
"config_id": "",
"public_key": "MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIDATABCgKCAQEAt9uYkHzaizNXg/S11ncTTLybkMtqrKW8gg6TyzbGWnRNROl9O+l1VZBLG0xiMt1mZbuStl8Lt3l1vlkMa92kgLjN+UfKmq3KhBEheN2uMmR0WpwV83kceVRmzr5lug4RyQ/xA6/OXK4NptDIT4L6CUTBWMyk2mmY0Cq9HyyrjdnHeAXWAcQGFEac7W4jTjONZqI+lgScPewS+cPFnz1hAD0IAqzj5X2mZVSfFGR3tDoIe42jw5wb6W2yi8zb3mgKrGtTBbw0Ppj0UgKrmdN5iFmfUQHLEzKAakDggLcBtrW1o5+4WMaZOLw8maU5byvjXu3F3i3GdQe8SKTYcVK5OQIDAQAB",
"extension": "sykffle",
"note_file_name": "RECOVER-${EXTENSION}-FILES.txt",
"note_full_text": ">> Introduction\n\nImportant files on your system was ENCRYPTED and now they have have \"${EXTENSION}\" extension.\nIn order to recover your files you need to follow instructions below.\n\n>> Sensitive Data\n\nSensitive data on your system was DOWNLOADED and it will be PUBLISHED if you refuse to cooperate.\n\nData includes:\n- Employees personal data, CVs, DL, SSN.\n- Complete network map including credentials for local and remote services.\n- Financial information including clients data, bills, budgets, annual reports, bank statements.\n- Complete datagrams/schemas/drawings for manufacturing in solidworks format\n- And more...\n\nPrivate preview is published here: http://zujgzbu5y64xbmvc42addp4lxkoosb4tslf5mehnh7pvqjpwxn5gokyd.onion/b21e1fb6-ff88-425b-8339-3523179a1e3e/886cf430a907bbe9a3fd38fb704d524dbd199c1b042ad6f65dc72ad78704e21\n\n\n>> CAUTION\n\nDO NOT MODIFY FILES YOURSELF.\nDO NOT USE THIRD PARTY SOFTWARE TO RESTORE YOUR DATA.\nYOU MAY DAMAGE YOUR FILES, IT WILL RESULT IN PERMANENT DATA LOSS.\nYOUR DATA IS STRONGLY ENCRYPTED, YOU CAN NOT DECRYPT IT WITHOUT CIPHER KEY.\n\n>> Recovery procedure\n\nFollow these simple steps to get in touch and recover your data:\n1) Download and install Tor Browser from: https://torproject.org/\n2) Navigate to: http://mu75ltv3lxd24dbyu6gtvmnwybecigs5auki7fces437xvvflzva2nqd.onion/?access-key=${ACCESS_KEY}",
"note_short_text": "Important files on your system was ENCRYPTED.\nSensitive data on your system was DOWNLOADED.\nTo recover your files and prevent publishing of sensitive information follow instructions in \"${NOTE_FILE_NAME}\" file.",
"default_file_mode": {
"SmartPattern": [31457280, 10]
},
"default_file_cipher": "Best",
"credentials": [
["KELLERSUPPLY\\Administrator", "d@gw00d"],
["KELLERSUPPLY\\AdminRecovery", "K3ller!$Supp1y"],
[".\\Administrator", "d@gw00d"],
[".\\Administrator", "K3ller!$Supp1y"]
],
"kill_services": ["mepocs", "memtas", "veeam", "svc$", "backup", "sql", "vss", "msexchange", "sql*"],
"kill_processes": ["encsvc", "thebat", "mydesktopqos", "xfssvccon", "firefox", "infopath", "winword", "steam", "synctime", "notepad", "ocomm", "onenote", "mspub", "thunderbird", "agntsvc", "sql", "excel", "powerpnt", "outlook", "wordpad", "dbeng50", "isqlplussvc", "sqbcoreservice", "oracle", "ocautoupds", "dbsnmp", "msaccess", "tbirdconfig", "ocssd", "mydesktopservice", "visio", "sql*"],
"exclude_directory_names": ["system volume information", "intel", "$windows.~ws", "application data", "$recycle.bin", "mozilla", "program files (x86)", "program files", "$windows.~bt", "public", "msocache", "windows", "default", "all users", "tor browser", "programdata", "boot", "config.msi", "google", "perflogs", "appdata", "windows.old"],
"exclude_file_names": ["desktop.ini", "autorun.inf", "ntldr", "bootsect.bak", "thumbs.db", "boot.ini", "ntuser.dat", "iconcache.db", "bootfont.bin", "ntuser.ini", "ntuser.dat.log"],
"exclude_file_extensions": ["themepack", "nls", "diagpkg", "msi", "lnk", "exe", "cab", "scr", "bat", "drv", "rtp", "msp", "prf", "msc", "ico", "key", "ocx", "diagcab", "diagcfg", "pdb", "wpx", "hlp", "icns", "rom", "dll", "msstyles", "mod", "ps1", "ics", "hta", "bin", "cmd", "ani", "386", "lock", "cur", "idx", "sys", "com", "deskthemepack", "shs", "ldf", "theme", "mpa", "nomedia", "spl", "cpl", "adv", "icl", "msu"],
"exclude_file_path_wildcard": [],
"enable_network_discovery": true,
"enable_self_propagation": false,
"enable_set_wallpaper": true,
"enable_esxi_vm_kill": true,
"strict_include_paths": []
}
枚举内网IP地址,探测有效IP以便于远程加密。
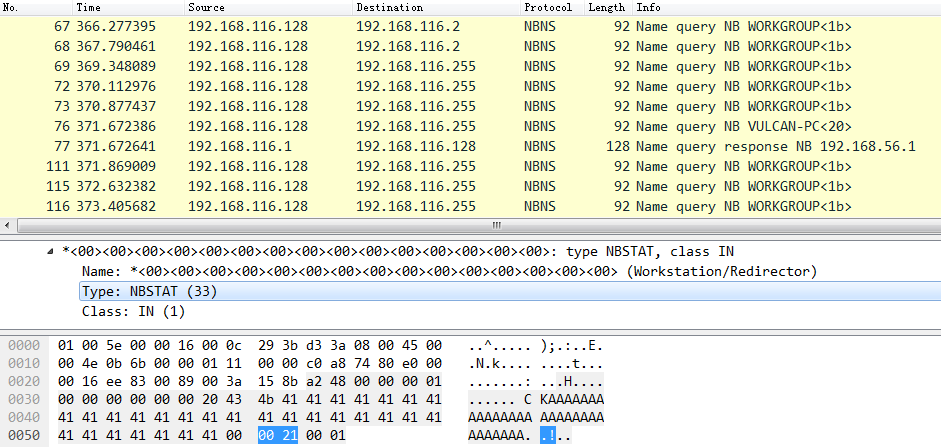
通过发送NBNS广播包请求获得远程计算机的响应
通过CMD执行“wmic csproduct get UUID”获得一个唯一硬件ID值,该值经过Base64编码转换为受害主机UID标识。

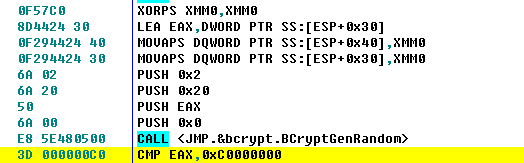
通过BCryptGenRandom生成0x20字节的随机数
使用ChaCha20算法加密文件
调用cmd.exe执行vssadmin删除卷影拷贝

将勒索版本信息,文件加密私钥数据,原始文件大小等信息组成一个JSON格式作为单个文件的解密配置。
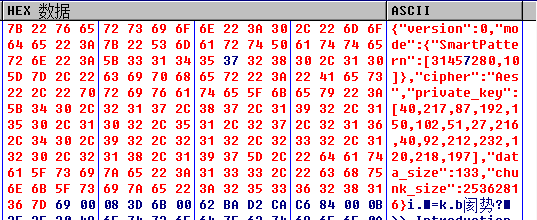
生成随机字符串将配置信息填充至0x100字节,通过RSA公钥将该段内容加密,并追加写入到文件末尾

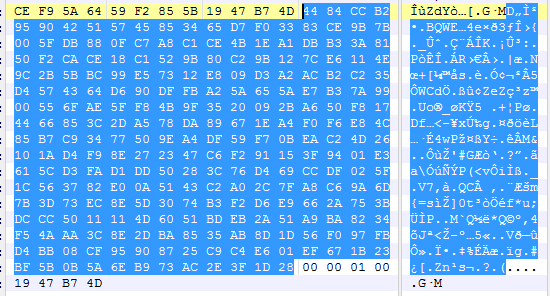
文件尾以两个0x4DB74719作为感染标识包含在被加密的文件密钥信息首尾位置。
释放勒索信到当前目录RECOVER-[扩展名]-FILES.txt, 勒索信的内容由之前的JSON数据进行控制。

处置及防范建议
参见瑞星勒索病毒防御指南:http://it.rising.com.cn/dongtai/19780.html
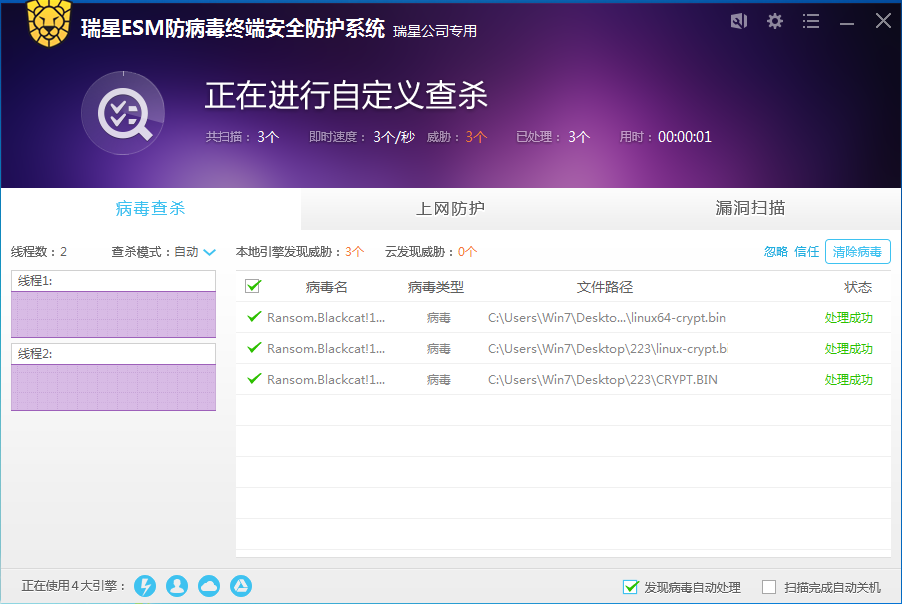
目前,瑞星ESM防病毒终端安全防护系统等产品可拦截并查杀相关勒索病毒,广大用户可安装瑞星的安全产品来规避相应风险。